Governance, Compliance, or Beyond? - Know your data
External attackers and insiders are a constant threat to corporate IT security posing
the biggest and most systemic risk to the global business.
Enterprise IT environments are large. It is natural to protect the most important IT assets with more layers of defence. Governance should ensure that access is limited to those who really need it (user access rights, access restrictions via networks micro-segmentation, etc.). Unfortunately, corporate IT is complex and some of the critical knowledge is always lost over time. Therefore, discovery of the data, data flows, business applications is the first necessary step to implement proper corporate-wide security-related governance.
In fact, the latest report from Verizon Enterprise Security Solutions on Data Breach Investigations identifies "Insider and Privilege Misuse" as the second most common reason of corporate security accidents and breaches: second only to truly accidental "Miscellaneous errors". Moreover, the number one recommendation to mitigate this risk is to "know your data" (
The White House is promoting network segmentation too.
I am X-standard compliant. I am fine, right?
PCI DSS v3+ and other security standards require data environments and data flows identification but do not be tricked:
almost any diagram provided to the security assessors will be enough to mark the corresponding check box.
Manual audits and interviews-driven data flows diagramming are only as accurate as IT personnel remembers the situation.
If you want true security going beyond marking checkboxes for compliance go for an automated data discovery and classification with modelizeIT.
A real-life example
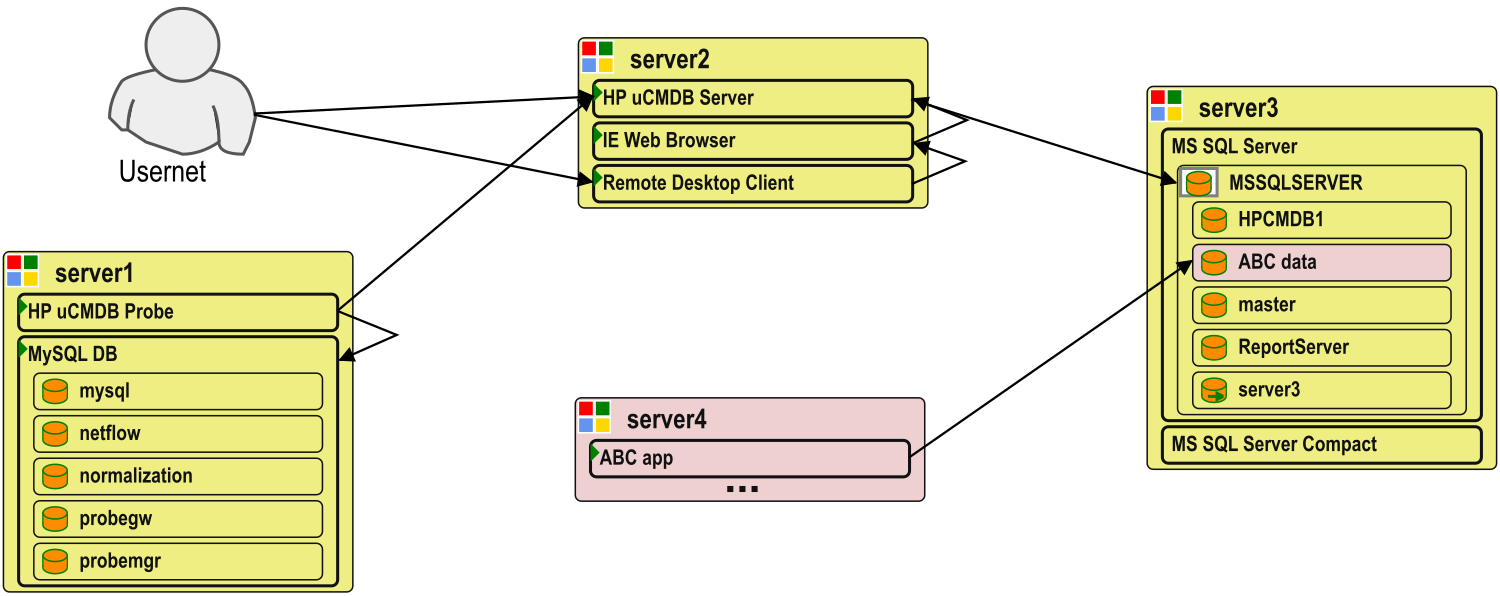
Example of an automatically-generated application diagram. Information collected from three servers belonging to an HP uCMDB deployment showed that its dedicated MS SQL server was, in fact, also used by another business application to keep its business-critical data. This is a common example of undocumented database usage.
Instead of consuming your IT personnel's time asking questions that they cannot answer, we analyze business application topologies automatically
(we certainly utilize the IT staff knowledge but only if it is available).
 Layered defense is the time-proven security mechanism.
Layered defense is the time-proven security mechanism.